Install primary dependencies (git and python)
Clone this repository
Run the tool
wget https://raw.githubusercontent.com/KasRoudra/PyPhisher/main/pyphisher.py && python3 pyphisher.py
Options
usage: pyphisher.py [-h] [-p PORT] [-o OPTION]
[--update | --no-update]
options:
-h, --help show this help message and exit
-p PORT, --port PORT PyPhisher's server port [ Default : 8080 ]
-o OPTION, --option OPTION
PyPhisher's template index [ Default : null ]
--update, --no-update
Check for update (default: True)
Features:
- Multi-platform (Supports most Linux)
- 65 Website templates
- Dual Tunneling (Ngrok and Cloudflare)
- Easy to use
- Possible error diagnoser
- Built-in masking of URL
- Custom masking of URL
- Portable file (Can be run from any directory)
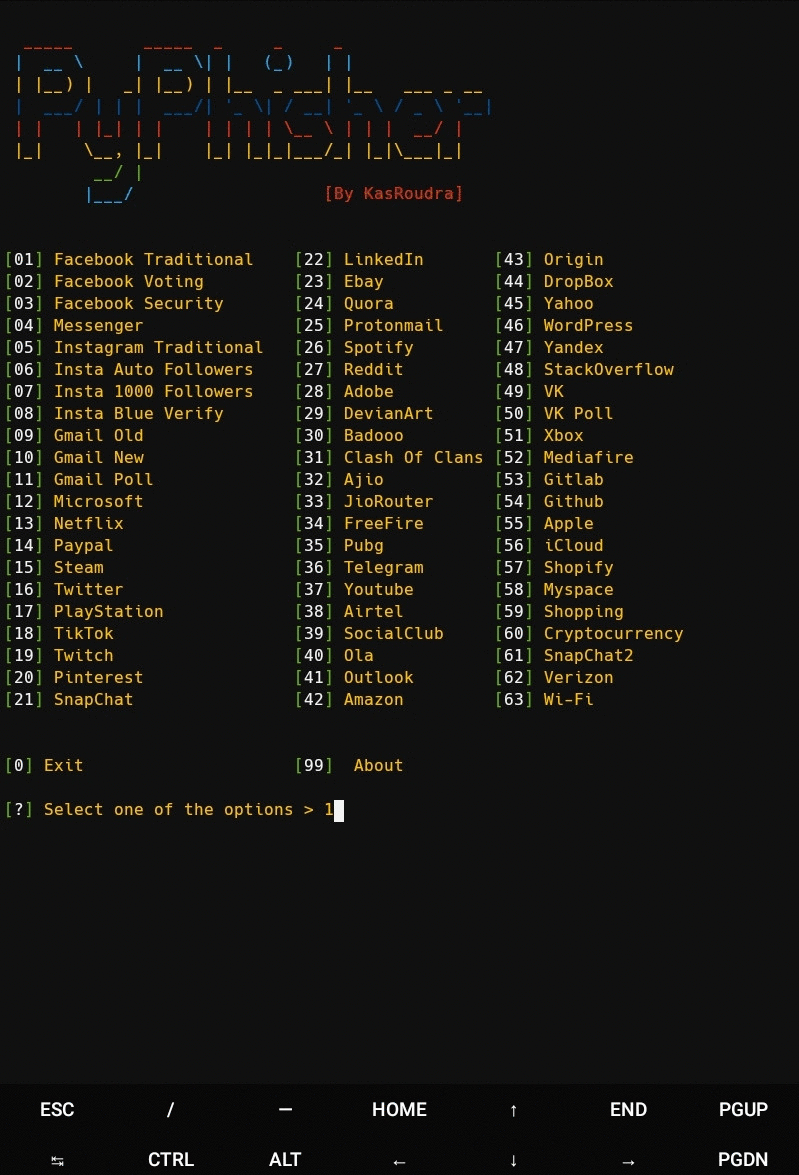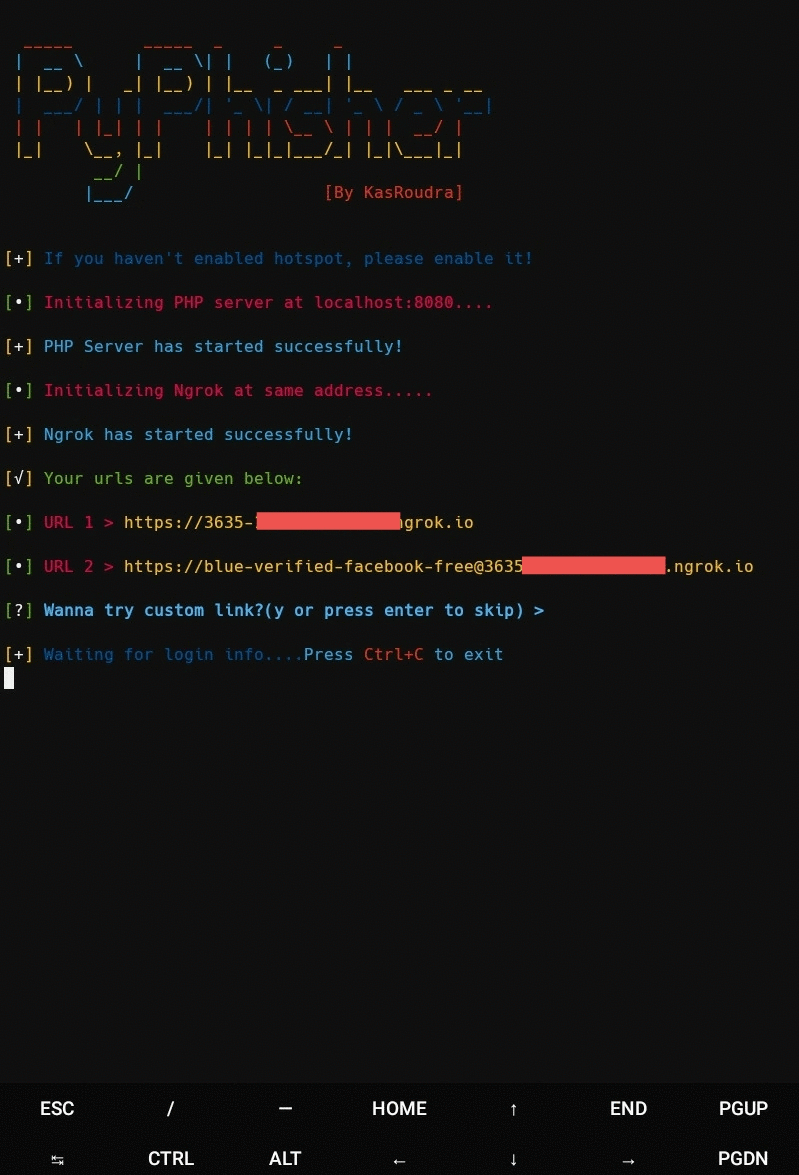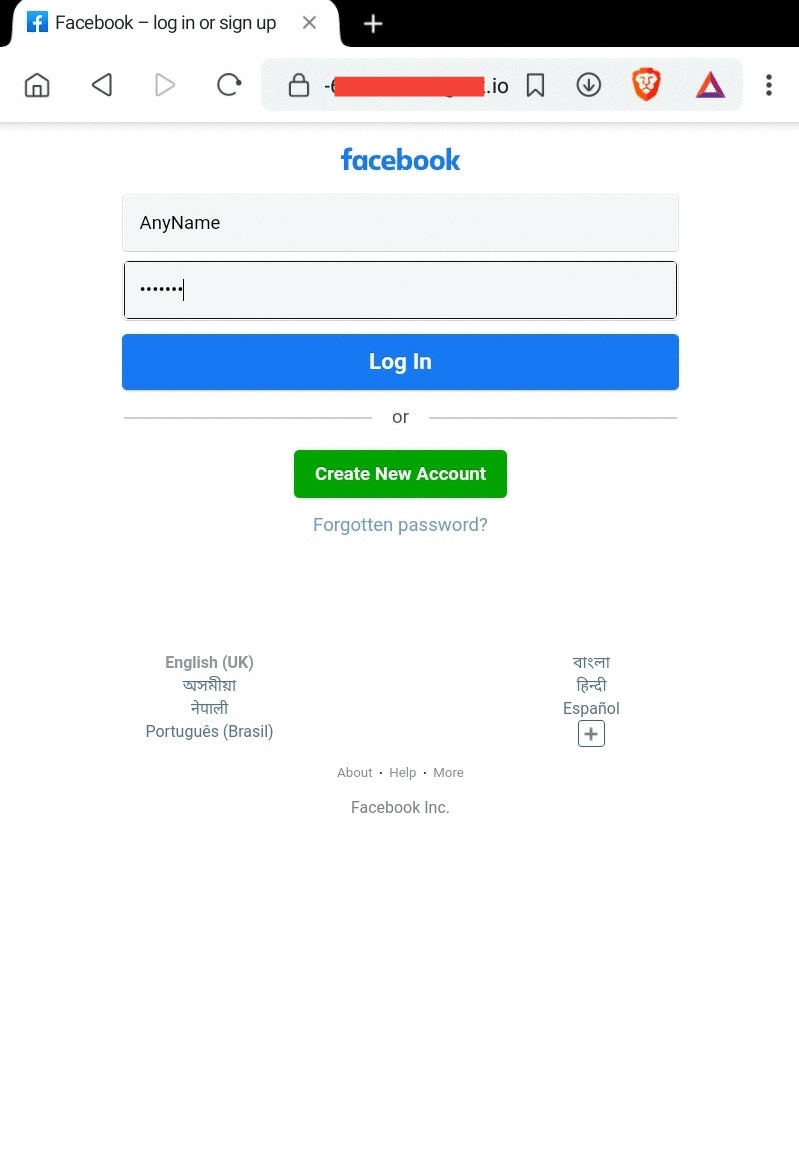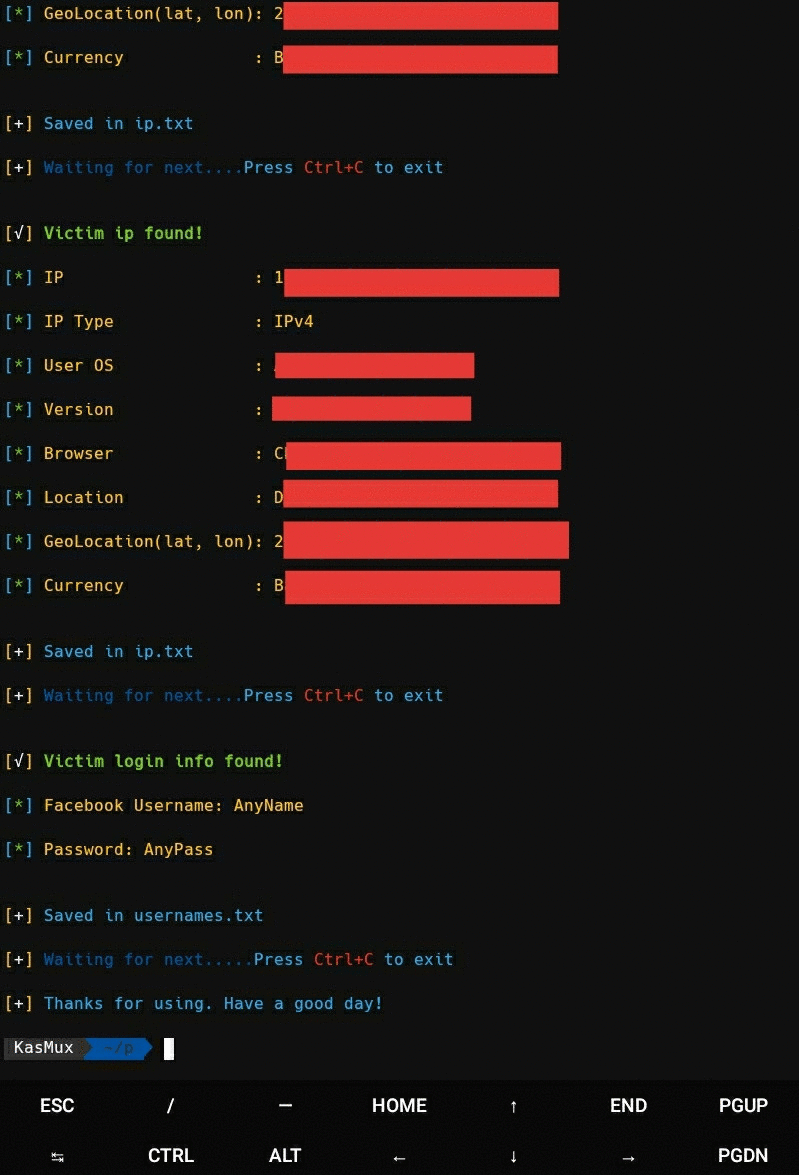
- Get IP Address and many other details along with login credentials
Requirements
Python(3)PHPCurlUnzipWget- 100MB storage
If not found, all of the required packages will be installed on the first run
Tested on
TermuxKali-Linux
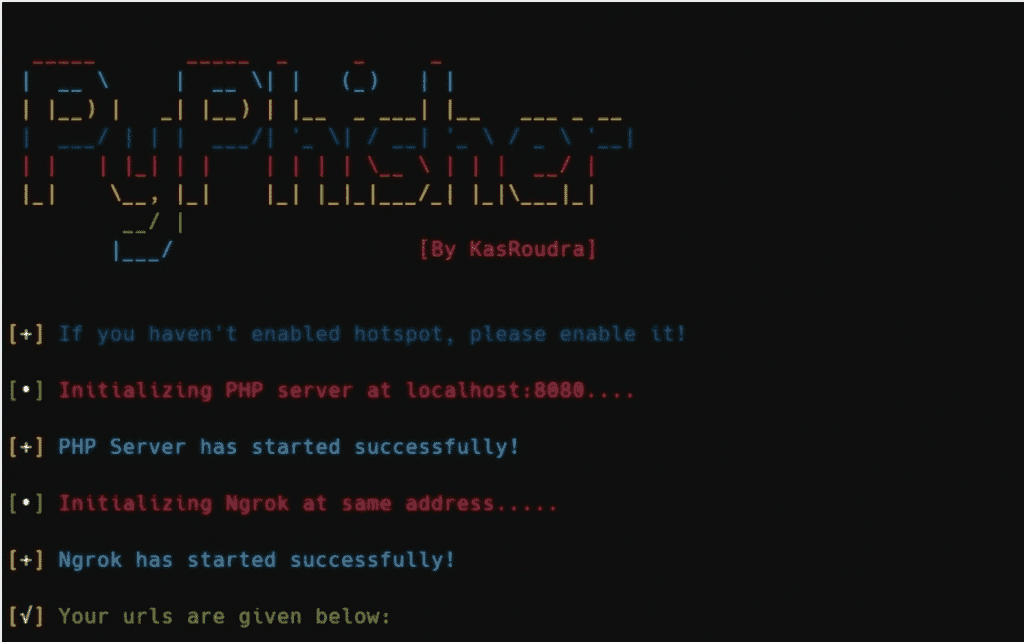
Usage
- Run the script
- Choose a Website
- Wait sometimes for setting up all
- Send the generated link to the victim
- Wait for victim login. As soon as he/she logs in, credentials will be captured
Example
Video Tutorial
Disclaimer
This tool is developed for educational purposes. Here it demonstrates how phishing works. If anybody wants to gain unauthorized access to someone’s social media, he/she may try out this at his/her own risk. You have your own responsibilities and you are liable to any damage or violation of laws by this tool. The author is not responsible for any misuse of PyPhisher!
This repository is open source to help others. So if you wish to copy, consider giving credit!
Credits: HTR-Tech and JayKali
If this tool helped you, consider starting a repository. Your stars encourage me a lot!
Find Me on:
usage: pyphisher.py [-h] [-p PORT] [-o OPTION]
[--update | --no-update]
options:
-h, --help show this help message and exit
-p PORT, --port PORT PyPhisher's server port [ Default : 8080 ]
-o OPTION, --option OPTION
PyPhisher's template index [ Default : null ]
--update, --no-update
Check for update (default: True)
Features:
- Multi-platform (Supports most Linux)
- 65 Website templates
- Dual Tunneling (Ngrok and Cloudflare)
- Easy to use
- Possible error diagnoser
- Built-in masking of URL
- Custom masking of URL
- Portable file (Can be run from any directory)
- Get IP Address and many other details along with login credentials
Requirements
Python(3)PHPCurlUnzipWget- 100MB storage
If not found, all of the required packages will be installed on the first run
Tested on
TermuxKali-Linux
Usage
- Run the script
- Choose a Website
- Wait sometimes for setting up all
- Send the generated link to the victim
- Wait for victim login. As soon as he/she logs in, credentials will be captured
Example
Video Tutorial
Disclaimer
This tool is developed for educational purposes. Here it demonstrates how phishing works. If anybody wants to gain unauthorized access to someone’s social media, he/she may try out this at his/her own risk. You have your own responsibilities and you are liable to any damage or violation of laws by this tool. The author is not responsible for any misuse of PyPhisher!
This repository is open source to help others. So if you wish to copy, consider giving credit!
Credits: HTR-Tech and JayKali
If this tool helped you, consider starting a repository. Your stars encourage me a lot!
Find Me on:
Features:
Requirements
If not found, all of the required packages will be installed on the first run
Tested on
Usage
This tool is developed for educational purposes. Here it demonstrates how phishing works. If anybody wants to gain unauthorized access to someone’s social media, he/she may try out this at his/her own risk. You have your own responsibilities and you are liable to any damage or violation of laws by this tool. The author is not responsible for any misuse of PyPhisher!
This repository is open source to help others. So if you wish to copy, consider giving credit!
If this tool helped you, consider starting a repository. Your stars encourage me a lot!
Find Me on:
This content was originally published here.